My Path of Binary Exploitation (1)

Preface⌗
It is the [insert an arbitrary number] time I have determined to learn binary exploitation since April 2017. However I have always lost intention as the problems are much more challenging than I am capable of. I could hardly remember anything on the next time when I have determined to study again. That's an incentive for me to write blog posts - I could read them and recall what has happened, thus spending less time learning all over from zero. Of course, it would be always better if I could persist.
This is the first part of myself solving binary exploitation challenges, and I could not guaranteed there will be follow-ups.
Getting "started" in pwnable.tw⌗
As I remember, this is my third time solving "Start" in pwnable.tw. But it is always refreshing for me as I am so forgetful... and I have never write walkthroughs while I learn pwnables.
The primary goal for binary exploitation challenges (pwnables) is to get access to the shell of a remote server. For web challenges in CTF, this could be achieved by identifying RCE (remote code execution) vulnerabilities. For pwnables, one way would be injecting shellcodes owing to stack overflow.
To begin with start, we use GNU debugger to perform static analysis on the binary:
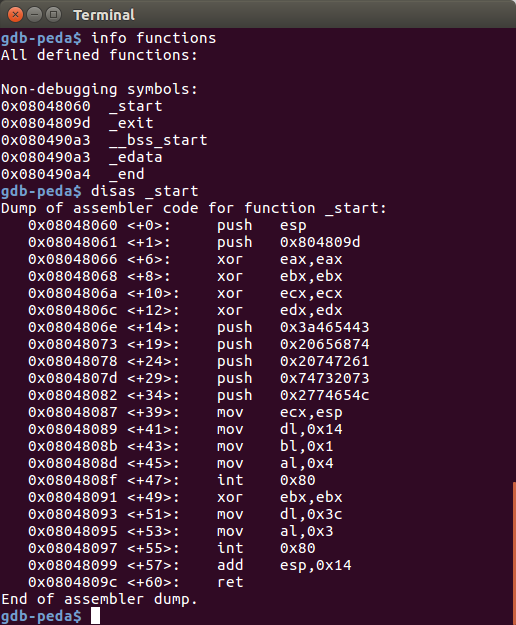
As an amateur, I could not read assembly codes well. Let's annotate the code first.

It involves four parts:
*_start+0to*_start+12: push the current stack pointer and the return address (_exit) to the stack.*_start+14to*_start+47: push the string "Let's start the CTF" into the stack and print it to stdout.*_start+49to*_start+55: reads 60 bytes from stdin to the stack.*_stack+57to*_start+60: move the stack pointer by +20 bytes and continue executing the code in the corresponding address at the stack pointer.