Google CTF 2025 Quals Writeup
HKCERT CTF 2024 Quals Writeup (IV): The Reverse Challenges
HKCERT CTF 2024 Quals Writeup (III): The Web Challenges
HKCERT CTF 2024 Quals Writeup (II): Other Crypto Challenges
HKCERT CTF 2024 Quals Writeup (I): RSA LCG and Pigeon Post
NuttyShell CTF 2025: memo-ry
Chaining multiple bugs for the flag
BlazCTF 2024 Writeup
Hacking multiple Ethereum smart contracts.

HITCON CTF 2024 Writeup
The crypto challenge authors in HITCON 2024, @maple3142 and @_bronson113 prepared a set of exciting and difficult challenges.
I collaborated with @thehackerscrew1 as a guest player this time. In this blog post, we will cover three challenges: ZKPoF, PCBC Revenge and Hyper512.
Google CTF 2024 (III): IDEA
Related key attack on reduced-round IDEA
Google CTF 2024 (II): ZKPOK
MD5 in ZKP? YNGMI
Google CTF 2024 (I): Blinders
This is yet another edition of Google CTF, where I wrote some crypto challenges with my colleagues. I contributed on three challenges this time, namely, Blinders, ZKPOK and IDEA. There are respectively 56, 3 and 4 solves (out of 267 teams scoring non-zero flags) during the contest period.
Blinders is one of the challenges I coauthored, which introduces a protocol for private set membership.
Intigriti’s XSS Challenge (February 2024)
TetCTF 2024: adapt
Creating fake proofs on cosmos/iavl@v0.19.7
HKCERT CTF 2023 Postmortem (III): The Remaining Challenges

HKCERT CTF 2023 Postmortem (II): Harder Crypto Challenges

HKCERT CTF 2023 Postmortem (I): Easier Crypto Challenges

Firebird CTF 2024: Goldilocks
DownUnderCTF 2023 Writeup
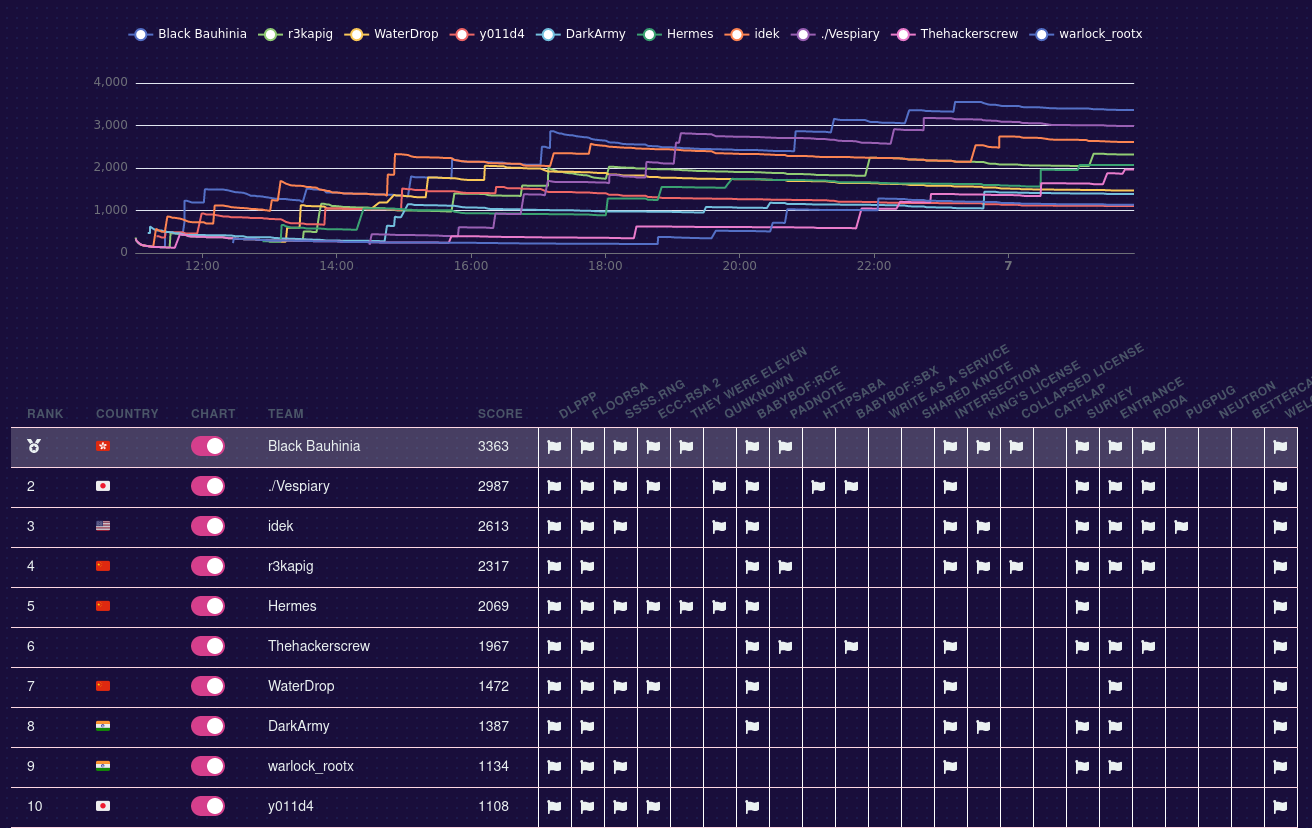
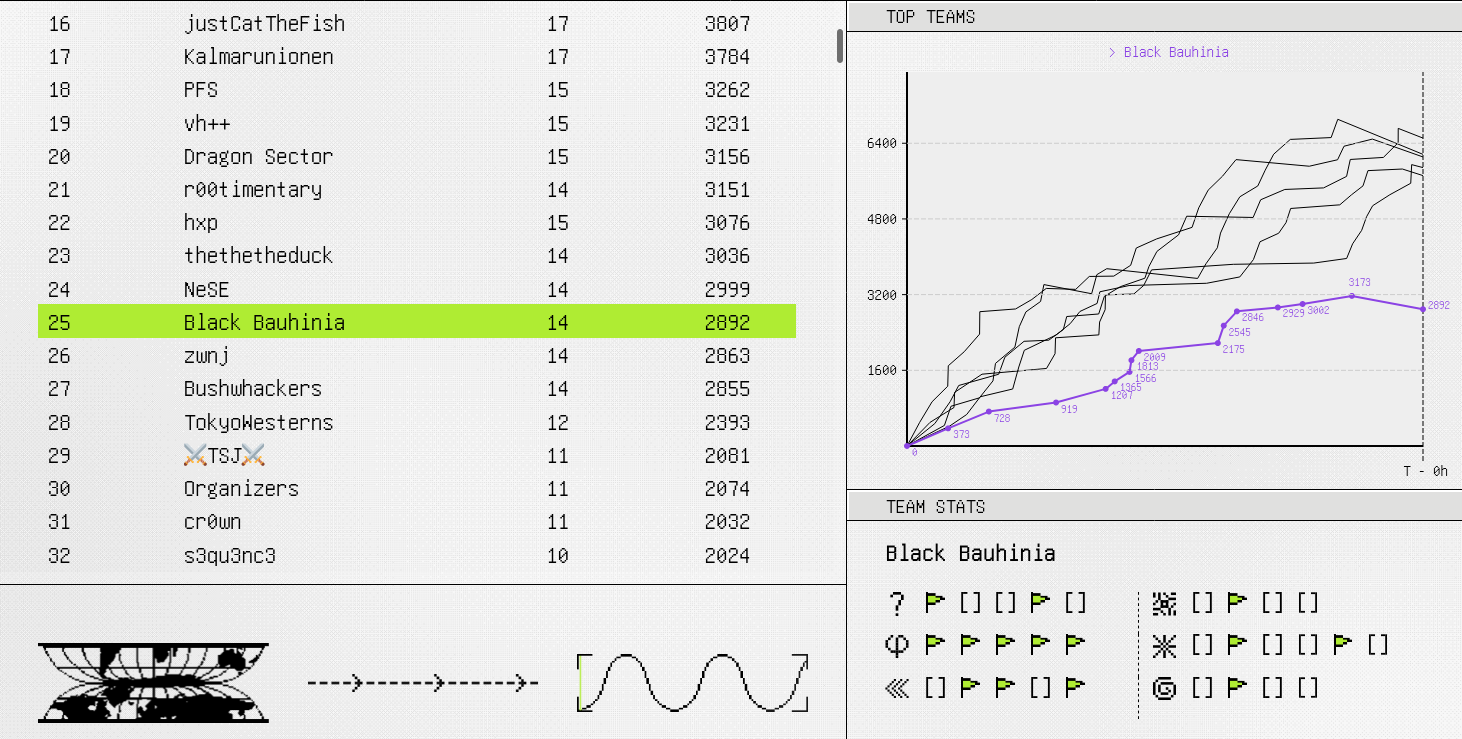
Bauhinia CTF 2023: How to Stop Time
After four years of team formation, we organized our first edition of Bauhinia CTF last weekend. There are over 650 teams registered and over 200 teams scored. This year, I made one crypto challenge, How to Stop Time. I also coauthored a web/crypto challenge, Amnesia, with @chthollic_.
This post is served as a short writeup of How to Stop Time, a crypto challenge with six solves during the contest period.
Google CTF 2023: MHK2
ACSC 2023 Quals (I): Gotion and easySSTI
Hacking Golang webapps with template injection & cache poisoning
Asian Cyber Security Challenge (ACSC) is an annual CTF where players are competing individually, and the best young Asians will be selected form a team to represent Asia to compete with others. I ended up winning the competition among 450+ players. Unfortunately, I am unable to qualify because of the age and nationality conditions.
In this blog post, I will cover two web challenges, @t0nk42’s easySSTI (43 solves) and @tyage’s Gotion (9 solves).
idekCTF 2022* Writeup
idekCTF 2022* definitely has a fun and inspiring set of cryptography challenges. I played with @blackb6a and we solved 8 of the 10 crypto challenges.
In this blog post, I’ll include my solution on three of them: Primonumerophobia (10 solves), Chronophobia (5 solves) and Decidophobia (3 solves).
MOCSCTF 2023 Postmortem

I prepared three challenges on behalf of @blackb6a for MOCSCTF, which is a 8-hour long CTF happened yesterday. This blogpost serves as the write-up for the three challenges that I wrote.
There are two solves (out of 40 participants) for Three-pass, and zero solves for jav-asr-ipt and Catch-22 Mini.
Firebird Internal CTF 2023 Writeup
Like in 2021 and 2022, I contributed some challenges for Firebird’s internal CTF, which are from the Hong Kong University of Science and Technology. This time I wrote three crypto challenges: Randomsum, Shelter and Threerider.
There were 24 teams participating. There were three solves for Randomsum, while Shelter and Threerider were unsolved during the CTF.
HKCERT CTF 2022 Postmortem (III): The Remaining Challenges
HKCERT CTF 2022 Postmortem (II): Harder Crypto Challenges

HKCERT CTF 2022 Postmortem (I): Easier Crypto Challenges
This is the third year Black Bauhinia co-organized HKCERT CTF. This time I wrote nine challenges: Seven crypto, one reverse and one misc.
Similar to the last year, I have a series of three blog posts walking through the challenges that I wrote. We will discuss the four easier crypto challenges: Flawed ElGamal, Catch-22, Rogue Secret Assistant and Base64 encryption.
H4CK1NG G00GL3 - Ep 005 Ch 002: Project Zero Adventure
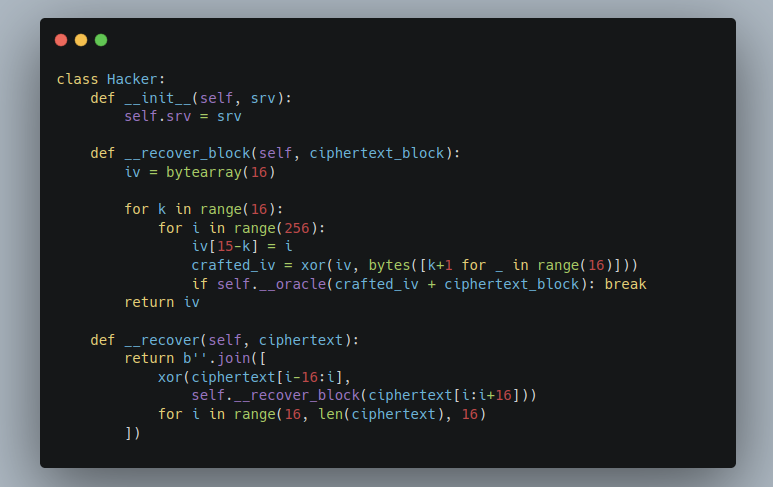
Bleichenbacher strikes back again (and again)
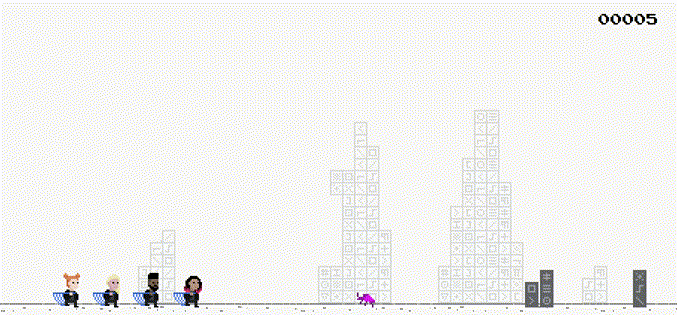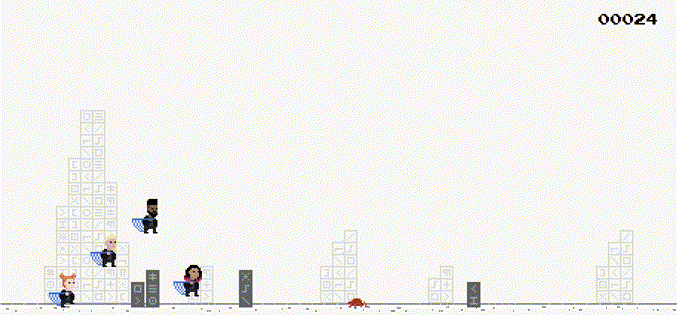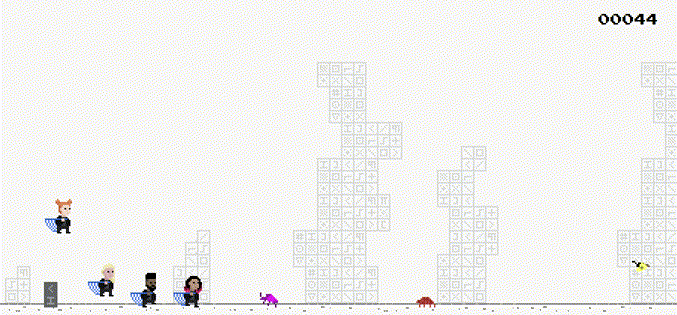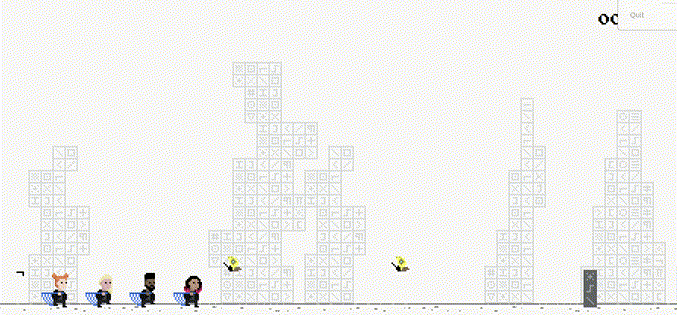
HACKING GOOGLE is a documentary of Google’s cybersecurity teams and H4CK1NG G00GL3 is it’s CTF counterpart. Project Zero Adventure is a cryptography challenge I wrote.
In the game, the players control the Security Princess to dodge the obstacles and catch the bugs (a variant of Google Chrome’s dinosaur game). After that, the server will sign messages consisting of the players' name and the score via the /sign API. The players will then submit it to the /highscore API. If the score submitted to the highscore API is negative, they will be given the flag.
However, there is one catch: The server is only willing to sign the results with non-negative scores.
BalsnCTF 2022 Writeup
vss is an interesting crypto challenge in BalsnCTF, which ended up having 9 solves. I took around 2.5 hours to solve the challenge. This challenge reminds me the yet another PRNG challenge from pbctf 2021, but with a setting which looked harder. I was pretty surprised that LLL worked, too.
lfsr is another crypto challenge in BalsnCTF with 6 solves. In the challenge, the output bits are computed nonlinearly from the LFSR states. Given that I knew almost nothing about LFSR, I just came up with the attack by myself… Well, I am not quite a paper guy and I couldn’t read.
Google CTF 2022: Maybe Someday
TSJ CTF 2022 (II): Signature
Breaking 256-bit ECDSA with $k = z \oplus d$ with only six signatures
TSJ CTF 2022 (I): Cipher Switching Service

@blackb6a played TSJ CTF and CODEGATE CTF this weekend. Both of the CTFs had a bunch of epic (and hard-ish) crypto challenges, which made our head scratched for days.
We were two points behind @balsnctf few minutes before the game ends and I found one more flag. It is proud to tell that we won TSJ CTF 🎉!
Anyway, I will compile writeups for (at least) three challenges for TSJ CTF, namely Cipher Switching Service, Signature and Genie. I will go through Cipher Switching Service as the first part of the series.
MOCSCTF 2022 Postmortem
Intigriti’s XSS Challenge (February 2022)
DiceCTF 2022 (I): commitment-issues
DiceCTF is an annual CTF competition prepared by @dicegangctf. The challenges are great and we had a lot of fun solving them. I might be compiling writeup for a number of them, which depends if I had time.
I will first cover on a crypto challenge called commitment-issues, which had 16 solves (out of 1127 participating teams). @grhkm2023 and I spent a good 3 to 4 hours working on this challenge.
Firebird Internal CTF 2022 Writeup
Intigriti’s XSS Challenge (January 2022)
Dragon CTF 2021: CRC Recursive Challenge (Warmup)
Balsn CTF 2021: dlog
pow method. @grhkm2023 and I spent a lot of time working on this challenge. Although we did not solve it, we actually learned a lot from the challenge and lost a pile of hair (maybe it is just me).
HKCERT CTF 2021 Postmortem (IV): The Remaining Ones
HKCERT CTF 2021 Postmortem (III): The Reverse Challenges
HKCERT CTF 2021 Postmortem (II): Harder Crypto Challenges
HKCERT CTF 2021 Postmortem (I): Easier Crypto Challenges
Black Bauhinia coorganized HKCERT CTF 2021 and helped 95% of the technical stuffs, including challenge setting, platform development, infrastructure and etc. I will be writing a series of blog posts talking about the contest, and the first four would be the writeups of the challenges those I wrote.
In the first blog post, we will be going through four easier crypto challenges: A Joke Cipher, Cipher Mode Picker, Key Backup Service 1 and Key Backup Service 2.
BSides Ahmedabad CTF 2021 Writeup
No, we did not win. I see that coming and took a screenshot during the game.
BSides Ahmedabad CTF 2021 is organized by @zer0pts. That implies that players could spend a day happily working on the challenges. I enjoyed working on the challenges a lot. I’ll go through the harder crypto challenges and the reversing challenge called Collapsed License in this blog post.
Factoring a special RSA modulus from ASIS CTF 2021 Quals
LagLeg is a crypto challenge in ASIS CTF Quals 2021. We are asked to factor a given $n$ with $n = (r^5 + s)(r + s)$ as part of the challenge. Hereby $r$ and $s$ are respectively 256 and 64 bits long. I think my approach used is very unique and creative - and definitely worth mentioning. It does not mean that it is a good approach, however.
I will record the exact steps I solved the challenge. However, I will update the bounds and prove the whole thing so that it looked more rigorous. The full code will be attached at the end of the blog post, too.
pbctf 2021: Seed Me & Yet Another RSA

I am playing as a part of @blackb6a this time for perfect blue’s annual pbctf. This time there are six crypto challenges and I first blooded 🩸 half of them. I solved five of them, and collaborated with TWY (who made 99% of the process) for Seed Me. In this blog post, I will cover Seed Me and Yet Another RSA. I tried to make the whole post beginner friendly, hence included more details than necessary.
I was originally going to discuss all of the crypto challenges, but I found it is too demanding and tiring.
UIUCTF 2021: phpfuck

Google CTF 2021 Quals Writeup
DEF CON CTF Quals 2021: Day 2
DEF CON CTF Quals 2021: Day 1
I played DEF CON CTF Quals once again with @Shellphish and we ended up at the 10th place. This blog post describes what actually was going on from my side. If you are looking for an informative blog post, this is not a good-read for you. There would be a little useful information, since I am just hanging around most of the time. I will even shamelessly copy some memes online to make the blog post looked rich in content.
After all, I am only able to solve nooombers (on day 1), qoo-or-ooo and back-to-qoo (on day 2). What happened on day 2 from my point of view is considerably more interesting.
PlaidCTF 2021: Leaky Block Cipher
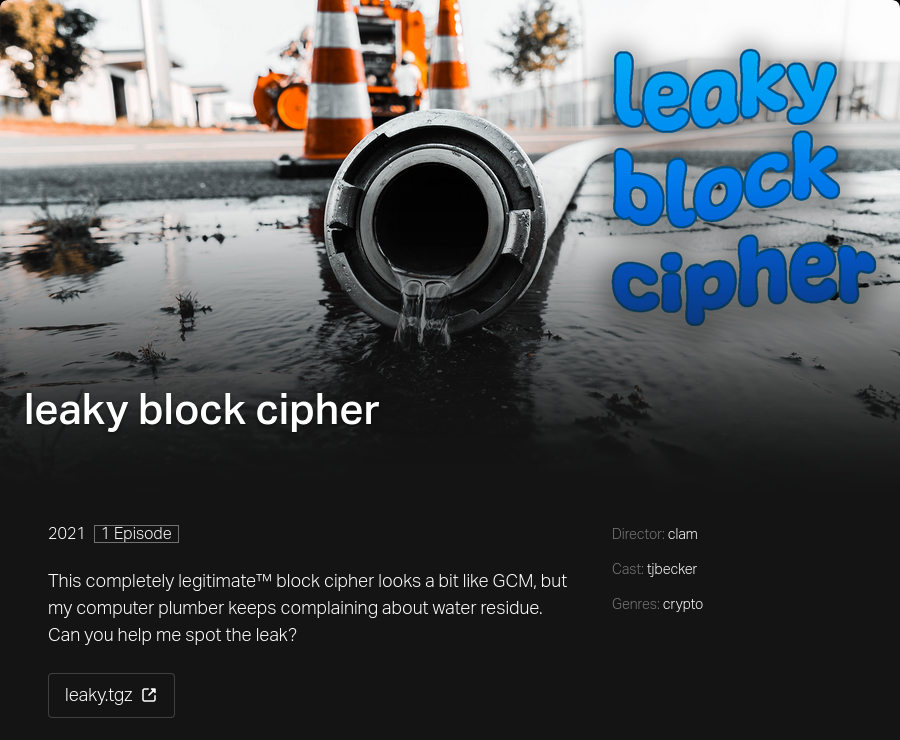
PlaidCTF this year had very insane challenges. Although I have spent a lot of time working on those crypto challenges, I was only able to solve leaky block cipher.
This completely legitimate™ block cipher looks a bit like GCM, but my computer plumber keeps complaining about water residue. Can you help me spot the leak? The challenge has a hand-crafted AEAD scheme. We are required to go through 20 rounds of challenges, and this is how each round proceeds…
ångstromCTF 2021: Cache Money
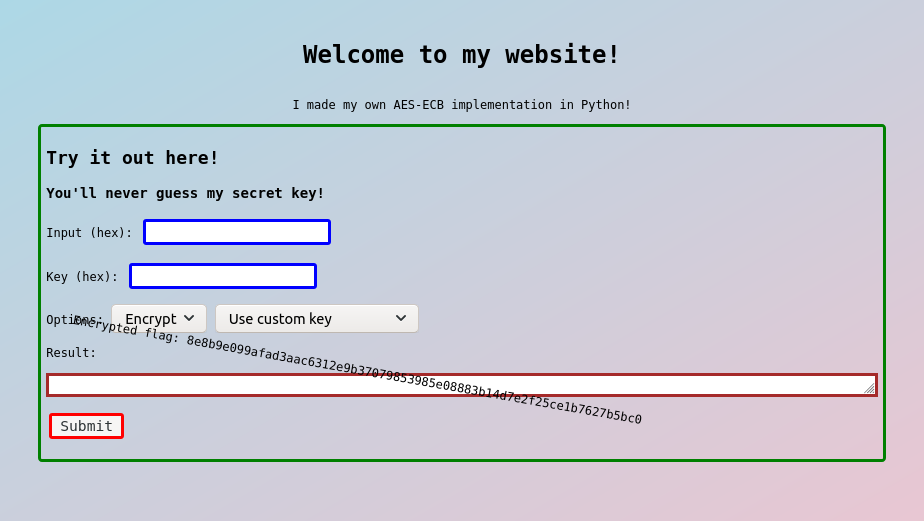
I played ångstromCTF 2021 for @blackb6a to spend my Easter holiday. I solved most of the reverse and cryptography challenges alone. In particular, Cache Money is one of the harder crypto challenges that I spent more than one day dealing with. It is very rewarding, and eventually four teams ended up solving it.
This challenge reimplements the Advanced Encryption Standard (AES) on 128, 192 and 256-bit keys. The encryptor is equipped with caches and we are given a service to encrypt (or decrypt) our messages. In short, there are four oracles provided by the service ($k_0$ is the fixed secret key and $b \in \{128, 192, 256\}$).
HKCERT CTF 2020 Postmortem
Aero CTF 2021 Writeup
Union CTF 2021 (II): committee
Union CTF 2021 (I): exah
kurenaif 1K Subscriptions Challenges
DiceCTF 2021 Writeup (I)
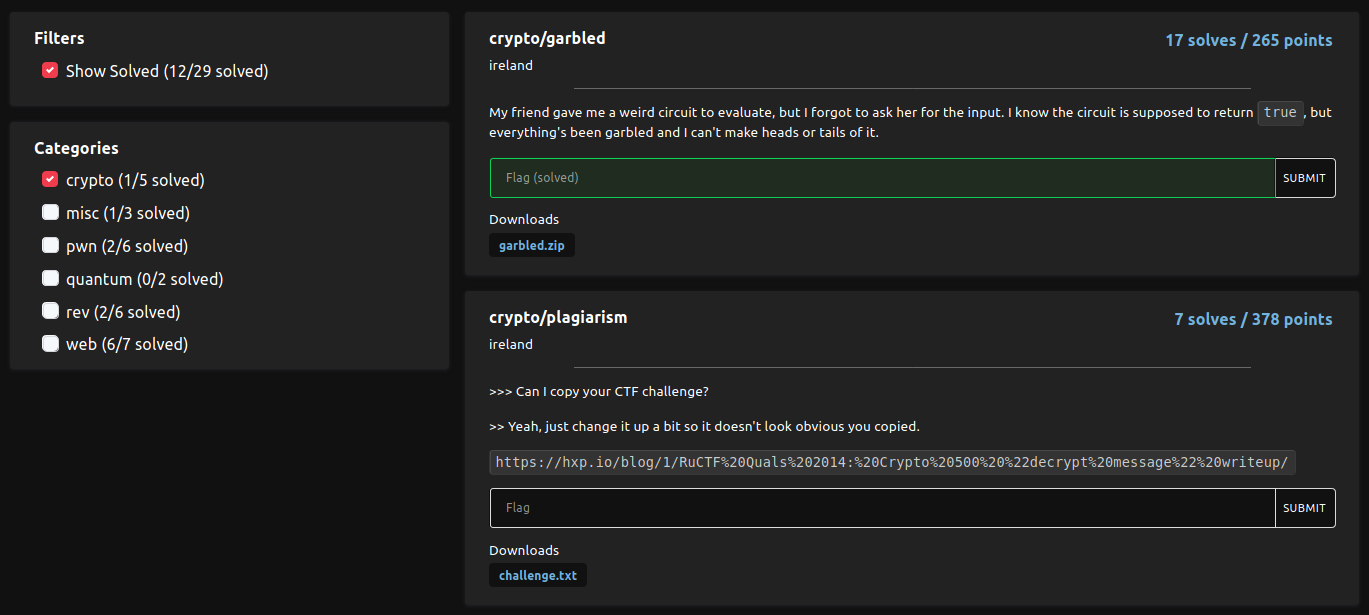
justCTF 2020: Oracles

hoifanrd’s osu! Challenge
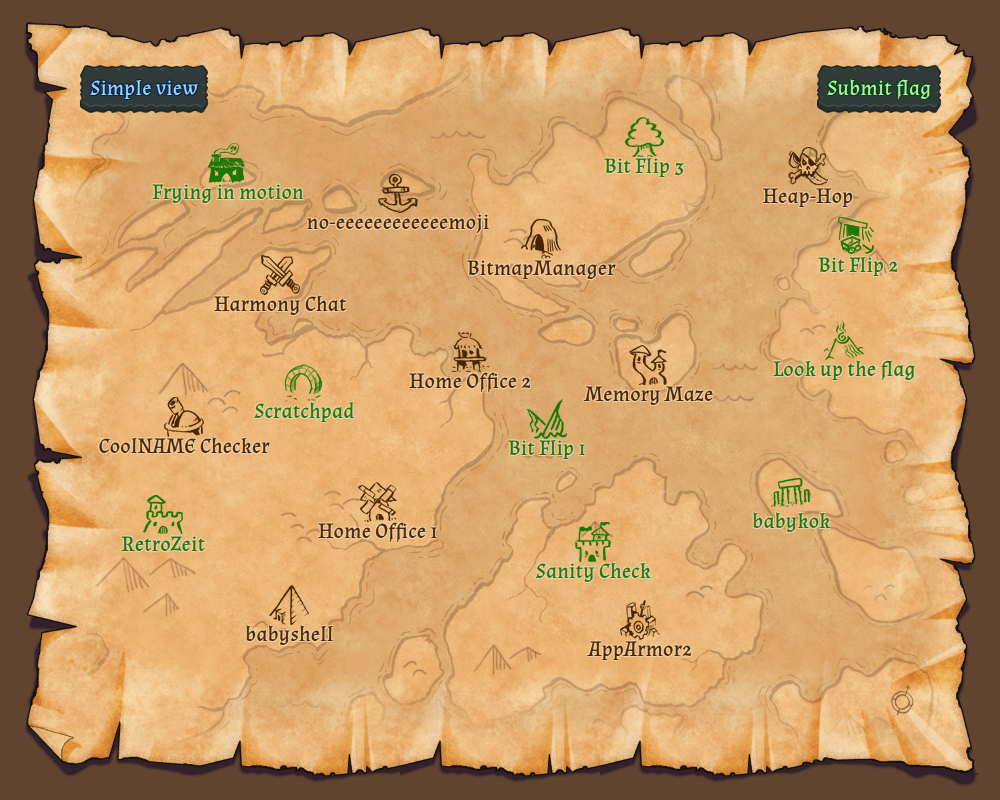
Firebird Internal CTF 2021 Writeup
TetCTF 2021: unevaluated
hxp CTF 2020: Hyper
Dragon CTF 2020 Writeup
Firebird Intro CTF: Rotten Secured Algorithm
CONFidence 2020 CTF: Team Trees
This week, we have teamed up as @blackb6a to play CONFidence 2020 CTF. We end up ranked 15, but we are more proud of ourselves able to solve a reversing challenge called Team Trees (395 points, 5 solves).
In particular, we are the first-to-solve to the challenge. It took us around two hours to win the flag. This writeup is written by @harrier_lcc and @mystiz613.
Google CTF 2020: Oracle
I was teamed-up with @blackb6a on Google CTF this time. I have solved 7 challenges alone and 3 challenges with my teammates.
In particular, Oracle is a crypto challenge with 13 solves. It has got me spending 12 hours. All in all, it was a great experience in terms of learning, but my liver hurts. This piece of writeup may be very computation intensive, just because I would like to make everything clear.
UIUCTF 2020: nookcrypt
nookcrypt is a netcat service that have no source code released. There are two functions exposed:
- Gets an encrypted copy of the flag (and the message hello world).
- Encrypts an arbitrary message.
De1CTF 2020 Writeup
I was teamed up with @shellphish this time for De1CTF. During the game, I have solved 5 (out of 7) cryptography challenges individually, and a reverse challenge and a misc challenge in cooperation with DuSu and fs0c.
I said that I’ll commit the solution scripts to my Github after I have managed to prettify them. It never happened. I will not make the same promise again.
PlaidCTF 2020: A Plaid Puzzle

De1CTF 2019 Writeup
It has been a very long time that I’ve compiled a writeup. This time I have played on my own as @blackb6a. Let me write on some particular interesting ideas that I have learnt in the challenges. Bear with me if you find this writeup too math-intensive.
The solution scripts will be committed to my Github repository sooner or later, after I’ve managed to prettify them.